What is blockchain technology? It’s a revolutionary system that uses cryptography to secure and verify transactions across a decentralized network. Imagine a digital ledger, shared publicly and replicated across numerous computers, making it virtually impossible to alter or delete information. This shared, transparent record forms the foundation of blockchain, enabling trust and security in a wide array of applications, from cryptocurrencies to supply chain management.
This technology operates on a principle of consensus, meaning all participants must agree on the validity of each transaction before it’s added to the blockchain. This process, coupled with cryptographic hashing, ensures the integrity and immutability of the data. We will explore the core concepts, different types of blockchains, their applications, and the future potential of this transformative technology.
Core Concepts of Blockchain
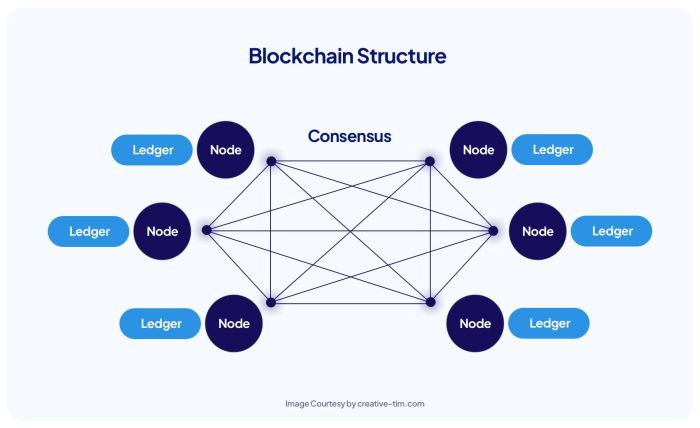
Blockchain technology is a revolutionary system for recording and verifying transactions in a secure and transparent manner. It’s built upon several key principles that differentiate it from traditional databases and systems. Understanding these core concepts is crucial to grasping its potential and limitations.
At its heart, a blockchain is a continuously growing list of records, called blocks, linked together using cryptography. Each block contains a set of validated transactions, a timestamp, and a cryptographic hash of the previous block. This chain-like structure ensures the integrity and immutability of the data. The distributed nature of the blockchain, across many computers, further enhances security and resilience.
Cryptography’s Role in Securing Blockchain Transactions
Cryptography is the backbone of blockchain security. It uses complex mathematical algorithms to ensure the confidentiality, integrity, and authenticity of transactions. Specifically, cryptographic hashing functions create unique digital fingerprints (hashes) for each block. Any alteration to the data within a block will result in a completely different hash, immediately revealing any tampering attempts. Furthermore, public-key cryptography allows users to securely send and receive transactions without revealing their private keys. This system relies on pairs of keys: a public key for verifying transactions and a private key for authorizing them.
Decentralization in Blockchain
Unlike traditional databases that are controlled by a central authority, blockchains are decentralized. This means that the data is not stored in a single location but is distributed across a network of computers (nodes). This distributed ledger technology eliminates single points of failure and makes the system more resistant to censorship and manipulation. The consensus mechanisms, such as Proof-of-Work or Proof-of-Stake, ensure that all nodes agree on the valid state of the blockchain, preventing fraudulent transactions from being added. Bitcoin, for instance, utilizes Proof-of-Work, requiring significant computational power to add new blocks and validate transactions, making it extremely difficult for a single entity to control the network.
Blockchain Transaction Processing
A blockchain transaction follows a specific process. First, a user initiates a transaction (e.g., sending cryptocurrency). This transaction is then broadcast to the network of nodes. Next, the nodes verify the transaction’s validity by checking the sender’s digital signature and ensuring sufficient funds. Once verified, the transaction is grouped with other transactions into a block. The block is then added to the blockchain after it’s validated by a consensus mechanism (e.g., miners in Proof-of-Work). Finally, the updated blockchain is propagated across the network, ensuring all nodes have a consistent copy of the ledger. This entire process ensures transparency, security, and immutability. For example, in Ethereum, smart contracts automate many aspects of this process, enabling decentralized applications (dApps) to execute automatically based on predefined conditions.
Types of Blockchains
Blockchains aren’t a one-size-fits-all solution. They come in various forms, each designed with specific goals and use cases in mind. The most prominent categorizations are public, private, and permissioned blockchains, each differing significantly in their architecture, accessibility, and security mechanisms. Understanding these differences is crucial for choosing the right blockchain for a particular application.
The core distinctions lie in who can participate in the network, how transactions are validated, and the level of transparency offered. These factors directly impact the blockchain’s security, scalability, and overall suitability for different applications.
Public Blockchains
Public blockchains, like Bitcoin and Ethereum, are open and decentralized. Anyone can participate, view transactions, and contribute to the network’s security. This open nature fosters transparency and trust, but also presents challenges regarding scalability and transaction speed. The consensus mechanism typically employed is Proof-of-Work (PoW) or Proof-of-Stake (PoS), aiming to ensure the integrity and immutability of the blockchain. PoW relies on computationally intensive tasks to validate transactions, while PoS requires users to stake their cryptocurrency to participate in validation.
Advantages of public blockchains include their high level of decentralization, transparency, and security. Disadvantages include slower transaction speeds, higher energy consumption (especially with PoW), and potential vulnerability to 51% attacks, although the probability decreases with network size and decentralization.
Blockchain technology, at its core, is a decentralized, secure ledger system. Understanding its fundamental structure requires some familiarity with the broader landscape of technologies involved in data management and security. Ultimately, blockchain’s strength lies in its ability to provide transparent and tamper-proof records, unlike many traditional systems.
Use cases best suited for public blockchains include cryptocurrencies, decentralized applications (dApps), and supply chain management where transparency and immutability are paramount.
Private Blockchains
Private blockchains are the opposite of public blockchains; they are centralized and permissioned. Access is restricted to authorized participants, and only those with permission can read and write data. This provides greater control and privacy but sacrifices the decentralization and transparency benefits of public blockchains. Consensus mechanisms can vary, often employing simpler and faster methods than those used in public blockchains, such as Practical Byzantine Fault Tolerance (PBFT) or Raft.
Advantages of private blockchains include improved speed and efficiency, enhanced privacy, and greater control over the network. Disadvantages include the risk of single points of failure, reduced transparency, and potential for manipulation by the controlling entity.
Use cases best suited for private blockchains include internal data management within organizations, supply chain tracking within a closed ecosystem, and managing sensitive information where privacy is crucial.
Permissioned Blockchains
Permissioned blockchains represent a middle ground between public and private blockchains. They are partially decentralized, meaning access is restricted to a predefined set of participants, but the network is not controlled by a single entity. This allows for a balance between transparency, security, and control. Permissioned blockchains often utilize hybrid consensus mechanisms, combining elements of PoW, PoS, and other algorithms tailored to the specific needs of the network.
Advantages of permissioned blockchains include a balance between decentralization and control, enhanced security compared to private blockchains, and faster transaction speeds than public blockchains. Disadvantages include the potential for collusion among participants and the complexity of managing permissions and access control.
Use cases best suited for permissioned blockchains include inter-organizational collaborations, managing shared resources within a consortium, and building decentralized applications requiring controlled access and enhanced privacy.
Blockchain technology, at its core, is a decentralized, secure ledger system. Understanding its fundamental structure requires some familiarity with the broader landscape of technologies involved in data management and security. Ultimately, blockchain’s strength lies in its ability to provide transparent and tamper-proof records, unlike many traditional systems.
Blockchain Consensus Mechanisms
Reaching a consensus in a decentralized network is crucial for the integrity and security of a blockchain. Without a robust mechanism to agree on the validity of transactions and the order in which they are added to the blockchain, the entire system would collapse. Various consensus mechanisms exist, each with its strengths and weaknesses regarding energy efficiency and security. This section explores two prominent mechanisms: Proof-of-Work (PoW) and Proof-of-Stake (PoS).
Proof-of-Work (PoW)
Proof-of-Work is the original consensus mechanism used by Bitcoin. It relies on a competitive process where miners compete to solve complex cryptographic puzzles. The first miner to solve the puzzle gets to add the next block of transactions to the blockchain and receives a reward in cryptocurrency. This process requires significant computational power, hence the “work” aspect. The difficulty of the puzzle adjusts dynamically to maintain a consistent block creation rate. A higher hash rate (the number of computations performed per second) across the network increases the difficulty, preventing manipulation. The extensive computational power required makes PoW highly secure, as it would require a majority of the network’s hash rate to successfully attack the blockchain.
Proof-of-Stake (PoS)
Proof-of-Stake offers a more energy-efficient alternative to PoW. Instead of competing for computational power, validators in a PoS system are selected based on the amount of cryptocurrency they stake. The more cryptocurrency a validator stakes, the higher the probability of being selected to validate the next block. This selection process is typically randomized, ensuring fairness and preventing centralization. Validators who act maliciously risk losing their staked cryptocurrency. PoS significantly reduces energy consumption compared to PoW because it eliminates the need for extensive computational power to solve complex cryptographic puzzles.
Energy Efficiency Comparison
The energy consumption of PoW is significantly higher than PoS. PoW systems, like Bitcoin, consume vast amounts of electricity due to the intense computational requirements of mining. Estimates vary, but the annual energy consumption of Bitcoin is often compared to the energy consumption of entire countries. In contrast, PoS systems consume considerably less energy, making them a more environmentally friendly option. The energy efficiency difference stems from the fundamental difference in how consensus is reached: PoW relies on brute-force computation, while PoS relies on a probabilistic selection process based on staked cryptocurrency. This difference leads to orders of magnitude variation in energy consumption. For example, Cardano, a PoS blockchain, boasts significantly lower energy consumption compared to Bitcoin.
Security Implications of Consensus Algorithms
The security of a blockchain is directly linked to its consensus mechanism. PoW’s security is derived from the vast computational power required to attack the network. An attacker would need to control more than 50% of the network’s hash rate to successfully alter the blockchain’s history, a computationally infeasible task for most attacks. However, the high energy consumption is a significant drawback. PoS, while more energy-efficient, relies on the economic incentive of validators not to act maliciously. A sufficiently large stake held by a malicious actor could compromise the network. Therefore, the security of PoS systems depends heavily on the distribution of staked cryptocurrency and the effectiveness of mechanisms to penalize malicious behavior. Both PoW and PoS have vulnerabilities; the choice of mechanism involves a trade-off between security and energy efficiency.
Reaching Consensus in a Decentralized Network
Reaching consensus in a decentralized network involves a complex process of communication and validation among nodes. In PoW, miners broadcast their solutions to the network. Once a miner finds a valid solution, they broadcast the new block containing the transactions to the network. Other nodes verify the block’s validity by checking the solution and the included transactions. If the majority of nodes validate the block, it is added to the blockchain. In PoS, validators are selected to propose and validate blocks. The process often involves a combination of random selection and weighted probability based on the staked amount. Similar to PoW, other nodes verify the proposed block. If a sufficient number of validators agree on the validity of the block, it is added to the blockchain. The specific implementation details of consensus vary between different blockchain networks, but the core principle remains the same: a decentralized agreement on the state of the blockchain through a process of validation and verification.
Blockchain Applications
Blockchain technology, with its inherent security and transparency, has far-reaching applications beyond cryptocurrencies. Its decentralized nature and immutable ledger offer solutions to various challenges across diverse sectors, improving efficiency, trust, and security. This section explores several key areas where blockchain is making a significant impact.
Blockchain in Finance
Blockchain’s impact on the financial industry is undeniable, most notably through cryptocurrencies like Bitcoin and Ethereum. These digital currencies utilize blockchain to record and verify transactions without the need for intermediaries like banks, fostering faster and potentially cheaper transactions. Beyond cryptocurrencies, blockchain is being explored for other financial applications, including streamlining cross-border payments, improving the efficiency of securities trading, and enhancing the security of digital assets. For example, Ripple uses blockchain technology to facilitate faster and more cost-effective international money transfers. Similarly, various companies are experimenting with blockchain-based platforms for managing digital securities, offering increased transparency and reduced fraud risk.
Blockchain in Supply Chain Management
Supply chains often involve multiple parties, making tracking products and verifying their authenticity challenging. Blockchain provides a solution by creating a shared, immutable record of a product’s journey from origin to consumer. This enhances transparency and traceability, allowing businesses to quickly identify and address potential issues like counterfeiting or product recalls. For example, a company could track the origin of coffee beans, verifying their ethical sourcing and fair trade practices. The ability to track every step in the supply chain, from farm to consumer, provides increased accountability and builds trust with consumers. Walmart, for instance, has implemented blockchain technology to enhance the traceability of its food products.
Blockchain in Healthcare Data Management
Healthcare data is highly sensitive, requiring robust security measures to protect patient privacy. Blockchain offers a secure and transparent way to manage medical records, allowing patients greater control over their data. By storing patient information on a decentralized blockchain, unauthorized access is minimized, and data integrity is ensured. This could streamline the sharing of medical records between healthcare providers, improve the efficiency of clinical trials, and facilitate secure data exchange between patients and their doctors. Imagine a scenario where a patient’s medical history is readily accessible to authorized healthcare professionals across different hospitals, eliminating the need for repeated tests and ensuring consistent care.
A Hypothetical Blockchain Solution for Secure Voting Systems
A secure and transparent voting system is crucial for a democratic society. A blockchain-based voting system could offer a solution to concerns about voter fraud and manipulation. Each vote would be recorded as a block on the blockchain, making it virtually impossible to alter or delete votes after they are cast. The decentralized nature of blockchain ensures that no single entity controls the voting process, fostering trust and transparency. This system would require careful design to ensure voter anonymity while maintaining the integrity of the voting process. It could incorporate cryptographic techniques to ensure that votes are verifiable but not directly linked to individual voters. The blockchain would serve as an immutable record of the votes cast, allowing for transparent and auditable election results. This would provide a high level of confidence in the accuracy and integrity of the election outcome.
Smart Contracts
Smart contracts are self-executing contracts with the terms of the agreement between buyer and seller being directly written into lines of code. They are stored on a blockchain and automatically execute when predefined conditions are met, eliminating the need for intermediaries like lawyers or notaries. This automation enhances efficiency, transparency, and security.
Smart contracts function by using a combination of code and cryptographic techniques. The code defines the agreement’s rules and conditions, while cryptography ensures the integrity and authenticity of the contract. When triggered by a specific event, the code automatically executes the agreed-upon actions, transferring funds or assets as specified. This process is transparent and auditable because all transactions are recorded on the blockchain.
Smart Contract Benefits, What is blockchain technology
The benefits of using smart contracts are significant. They offer increased efficiency by automating processes and reducing reliance on intermediaries. This automation also lowers costs associated with traditional contract execution. Furthermore, smart contracts enhance transparency due to their immutable nature on the blockchain, enabling all parties to verify the contract’s execution. The security provided by cryptography ensures that the contract cannot be tampered with.
Smart Contract Limitations
Despite their advantages, smart contracts have limitations. One key limitation is the potential for vulnerabilities in the code. Bugs or flaws in the smart contract’s code can lead to unintended consequences or even malicious exploitation. Another limitation is the legal enforceability of smart contracts, which remains a complex and evolving area of law. Jurisdictional issues can also arise, making it challenging to determine which legal system governs a particular smart contract. Finally, the complexity of coding and deploying smart contracts can be a barrier to entry for some users.
Smart Contract Applications
Smart contracts have a wide range of applications across various industries. In supply chain management, they can track goods and ensure authenticity, reducing fraud and improving efficiency. In finance, they facilitate decentralized finance (DeFi) applications, enabling peer-to-peer lending and automated trading. In the healthcare industry, they can securely store and manage patient medical records. In the voting system, they can help conduct secure and transparent elections, reducing the risk of fraud.
Smart Contract Scenario: Supply Chain Tracking
Imagine a scenario where a manufacturer uses a smart contract to track the shipment of goods. The contract is written to automatically release payment to the supplier upon confirmation of delivery by the recipient. This confirmation is achieved via a sensor-based system integrated with the blockchain. Once the goods reach their destination, a sensor triggers a signal to the blockchain, confirming delivery and automatically initiating the payment transfer to the supplier as stipulated in the smart contract. This eliminates delays and the need for manual verification and reconciliation.
Security and Challenges
While blockchain technology offers significant advantages in terms of transparency and security, it’s not without its vulnerabilities and challenges. Understanding these aspects is crucial for responsible development and implementation. This section explores the security risks, potential threats, mitigation strategies, and scalability issues inherent in blockchain networks.
Blockchain’s inherent security stems from its decentralized and cryptographic nature. However, various points of weakness can be exploited, highlighting the need for robust security measures and ongoing development to address emerging threats.
Security Vulnerabilities and Threats
Several vulnerabilities can compromise the security of a blockchain network. These range from attacks targeting the consensus mechanism to exploits of smart contracts and vulnerabilities in the underlying infrastructure.
For instance, 51% attacks, where a single entity controls more than half the network’s hashing power, can allow manipulation of transactions and the rewriting of blockchain history. Other threats include Sybil attacks, where malicious actors create numerous fake identities to influence the network, and double-spending attacks, aiming to spend the same cryptocurrency twice. Furthermore, vulnerabilities in smart contracts, often due to coding errors, can be exploited to drain funds or disrupt functionality. Finally, weaknesses in the infrastructure supporting the blockchain, such as exchanges or wallets, can become entry points for attackers.
Measures to Enhance Blockchain Security
Numerous strategies aim to bolster the security of blockchain networks. These include robust cryptographic algorithms, regular security audits of smart contracts, and the implementation of multi-signature wallets requiring multiple approvals for transactions. Furthermore, employing diverse consensus mechanisms, such as Proof-of-Stake (PoS) which requires a stake in the network to participate in consensus, can reduce the likelihood of 51% attacks. Finally, continuous monitoring and threat intelligence are crucial for identifying and responding to emerging security risks. Regular software updates and patches are also essential to address vulnerabilities discovered in the blockchain’s software.
Challenges in Scaling Blockchain Networks
Scaling blockchain networks to handle a large volume of transactions presents a significant challenge. The inherent limitations of blockchain’s consensus mechanisms, particularly Proof-of-Work (PoW), lead to slow transaction speeds and high energy consumption as the network grows. This necessitates exploring alternative solutions like sharding, which partitions the blockchain into smaller, more manageable parts, and layer-2 scaling solutions, which process transactions off-chain before committing them to the main blockchain. The trade-offs between security, decentralization, and scalability require careful consideration when designing and implementing scalable blockchain architectures. For example, the Ethereum network has faced scalability issues in the past, leading to high transaction fees during periods of high network activity. Solutions like layer-2 scaling protocols (e.g., Optimism, Arbitrum) have been developed to address this, allowing for faster and cheaper transactions.
Blockchain and Data Management
Blockchain technology offers a revolutionary approach to data management, significantly improving upon traditional methods by enhancing data integrity, transparency, and security. Its decentralized and immutable nature provides a robust foundation for trustworthy data handling across various sectors.
Data Integrity and Transparency Improvements
Blockchain’s decentralized structure, where data is replicated across multiple nodes, inherently improves data integrity. Any attempt to alter data on one node is easily detectable as it will differ from the consensus held across the network. This eliminates single points of failure and reduces the risk of data corruption or manipulation. Furthermore, the transparent nature of blockchain, where all transactions are recorded and publicly verifiable (depending on the type of blockchain), fosters trust and accountability. Users can independently verify the authenticity and integrity of data without relying on a central authority.
Immutability’s Role in Data Management
Immutability, a core characteristic of blockchain, means that once data is recorded on the blockchain, it cannot be altered or deleted. This creates an auditable and permanent record of all transactions and data changes. This is particularly valuable in scenarios requiring high levels of data integrity and accountability, such as supply chain management, where the history of a product’s journey needs to be accurately tracked and verified. The immutability ensures that any discrepancies or fraudulent activities can be easily identified and investigated.
Blockchain’s Enhancement of Data Security and Privacy
Blockchain enhances data security through cryptographic hashing and encryption techniques. Each block in the chain is linked to the previous one using cryptographic hashes, making it computationally infeasible to tamper with data without detection. Furthermore, depending on the implementation, blockchain can offer improved privacy through techniques like zero-knowledge proofs or confidential transactions. These techniques allow for verification of data without revealing sensitive information, enabling secure sharing and management of personal or sensitive data. For example, medical records could be stored on a blockchain, allowing authorized healthcare providers to access and share relevant information while maintaining patient privacy.
Comparison of Blockchain and Traditional Databases for Data Management
| Feature | Blockchain | Traditional Database |
|---|---|---|
| Data Integrity | High, due to decentralization and cryptographic hashing | Moderate to high, dependent on security measures implemented |
| Transparency | High, depending on the blockchain type (public vs. private) | Low to moderate, controlled by the database administrator |
| Immutability | High, data cannot be altered or deleted once recorded | Low, data can be modified or deleted |
| Security | High, due to cryptographic techniques and decentralization | Moderate to high, dependent on security measures implemented |
The Future of Blockchain
The future of blockchain technology is brimming with potential, promising transformative changes across numerous sectors. While challenges remain, ongoing innovation and increasing adoption suggest a significant role for blockchain in shaping the digital landscape of tomorrow. This section explores potential future developments, emerging trends, and the projected impact of blockchain on various industries.
Potential Future Developments and Innovations
Several key areas are poised for significant advancements. Scalability remains a crucial challenge, and solutions like sharding and layer-2 scaling solutions are expected to become increasingly sophisticated, allowing for faster and cheaper transactions. Interoperability, the ability for different blockchain networks to communicate and share data seamlessly, is another area of intense development. Cross-chain communication protocols are being refined, paving the way for a more interconnected blockchain ecosystem. Furthermore, the integration of artificial intelligence (AI) and machine learning (ML) with blockchain is expected to lead to more efficient and secure systems, capable of automating complex processes and improving decision-making. Quantum-resistant cryptography is also under development to safeguard blockchain networks against potential threats from future quantum computing capabilities.
Emerging Trends and Challenges to Widespread Adoption
Despite its potential, several factors could hinder widespread blockchain adoption. Regulatory uncertainty remains a significant obstacle, with varying legal frameworks across jurisdictions creating complexities for businesses seeking to implement blockchain solutions. The need for greater user-friendliness and simpler interfaces is also crucial for mass adoption. Many existing blockchain technologies are technically complex and require specialized knowledge to utilize effectively. Furthermore, the energy consumption of some blockchain networks, particularly those employing proof-of-work consensus mechanisms, raises environmental concerns. Addressing these challenges is vital for the broader acceptance and integration of blockchain technology.
Potential Impact on Various Industries
Blockchain’s potential impact spans diverse sectors. In finance, it promises to revolutionize payment systems, enhance security, and streamline cross-border transactions. Supply chain management can benefit from increased transparency and traceability, reducing fraud and improving efficiency. Healthcare could see improvements in data security and interoperability, facilitating better patient care and research. The digital identity sector is also poised for transformation, with blockchain enabling secure and verifiable digital identities. The voting process could be revolutionized with enhanced security and transparency. These are just a few examples of the transformative potential of blockchain across various industries.
Predicted Milestones in Blockchain Development
A timeline of predicted milestones illustrates the expected evolution of blockchain technology. While precise dates are difficult to predict, the following represents a plausible trajectory:
| Year | Milestone | Example/Real-life Case |
|---|---|---|
| 2024-2025 | Increased adoption of layer-2 scaling solutions | Wider implementation of solutions like Polygon and Lightning Network, leading to significant improvements in transaction speeds and costs on major blockchains like Ethereum. |
| 2026-2028 | Significant advancements in interoperability | Successful implementation of cross-chain communication protocols enabling seamless data exchange between different blockchain networks, facilitating decentralized applications (dApps) operating across multiple chains. |
| 2029-2031 | Widespread adoption of quantum-resistant cryptography | Integration of post-quantum cryptography algorithms into mainstream blockchain platforms to protect against attacks from future quantum computers. This could involve transitioning from existing cryptographic standards to new, more secure ones. |
| 2032 and beyond | Matured regulatory frameworks and increased mainstream adoption | Clearer regulatory guidelines and standardization across jurisdictions will encourage greater trust and adoption of blockchain technologies across various industries. This could lead to the integration of blockchain into everyday life, similar to the widespread adoption of the internet. |
Blockchain vs. Traditional Databases: What Is Blockchain Technology
Blockchain technology and traditional database systems represent fundamentally different approaches to data management. While both store and manage data, their architectures, security models, and functionalities differ significantly, leading to distinct advantages and disadvantages depending on the specific application. Understanding these differences is crucial for choosing the right technology for a given task.
Data Structure and Architecture
Traditional databases, typically relational databases like MySQL or PostgreSQL, employ a centralized architecture. Data is stored in structured tables with defined schemas, allowing for efficient querying and retrieval. A central server manages access and updates to the database, ensuring data consistency. In contrast, blockchain utilizes a decentralized, distributed ledger. Data is organized into blocks, chained together cryptographically and replicated across multiple nodes in a network. This eliminates a single point of failure and enhances data security. Each block contains a timestamp and a hash of the previous block, creating an immutable and transparent record of transactions.
Security and Immutability
Security is a key differentiator. Traditional databases rely on access controls and encryption to protect data, but vulnerabilities remain due to the centralized nature. A single point of failure (the central server) can be compromised, leading to data breaches or corruption. Blockchains, on the other hand, leverage cryptography to secure data. The cryptographic hashing and distributed nature make it extremely difficult to alter or delete data once it’s added to the blockchain. This immutability is a significant advantage for applications requiring high data integrity, such as supply chain management or digital identity verification.
Scalability and Performance
Scalability is another critical aspect. Traditional databases can scale vertically (by increasing the server’s resources) or horizontally (by adding more servers). However, scaling can be expensive and complex. Blockchain scalability is a more significant challenge. The consensus mechanisms used to validate transactions can limit the throughput of the network. While solutions like sharding are being developed to address this, blockchains currently generally offer lower transaction speeds compared to traditional databases. This makes them less suitable for applications requiring high-volume, real-time data processing, such as online gaming or high-frequency trading.
Advantages and Disadvantages in Use Cases
Consider supply chain management. A blockchain provides a transparent and tamper-proof record of product movement, enhancing traceability and accountability. A traditional database, while capable of tracking this information, is vulnerable to manipulation. Conversely, for an e-commerce website processing thousands of transactions per second, a traditional database’s speed and scalability would be far superior to a blockchain’s capabilities.
Architectural Differences: A Visual Representation
Imagine two diagrams. The first, representing a centralized database, shows a single, large circle labeled “Central Database Server.” Arrows point from various devices (laptops, phones, etc.) to this central server, indicating data requests and updates. The second diagram, representing a blockchain network, depicts multiple smaller circles (nodes) interconnected in a network. Arrows show data flowing between these nodes. Each node holds a copy of the entire blockchain (a chain of interconnected blocks). New blocks are added to the chain, and the updated chain is propagated across the network. The decentralized nature of the blockchain network is clearly contrasted with the centralized architecture of the traditional database. This visual representation highlights the fundamental difference in how data is stored, managed, and accessed.
Final Summary
In conclusion, blockchain technology presents a paradigm shift in data management and security. Its decentralized, transparent, and secure nature holds immense potential across numerous sectors. While challenges remain in scalability and regulation, the ongoing innovation and development in this field promise a future where trust and efficiency are significantly enhanced through the power of distributed ledger technology. Understanding blockchain’s fundamentals is crucial for navigating the evolving technological landscape and harnessing its transformative capabilities.





